IAM
Identity and Access Management
Overview
IAM

How a service assume role
IAM policy
AWS access levels

Syntax
IAM provision workflow

Other policies
4 types of policy
IAM Roles vs Resource-based policies

IAM role & Resource-based policies
Features
Permission boundary
Policy evaluation logic

IAM Access Analysis
Benefits
How it works?
IAM credentials report
Use cases

Best practices
Top-10 security items to improve your AWS account
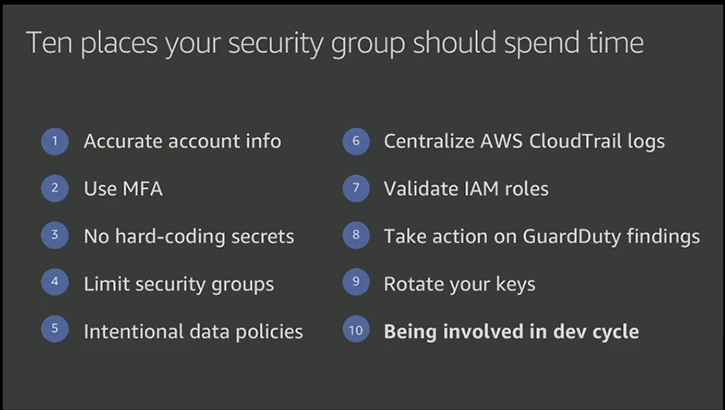
Security best practices
Trivia
Last updated
